Burp Intruder (part of the Burp Suite) is great tool for automating attacks against a web target. Intruder makes it possible to easily manipulate and enumerate imputs and perform automated brute-force attacks. This article will walk you through how I utilized Intruder to save me some time with the 'Reportinator' challenge that was part of the 2023 SANS Holiday Hack. The hack is still available for testing against today so I encourage you to try it yourself as you follow along.
If you are having trouble making out any of the images, clicking on them should open up a full screen version of them to make it easier to see.
WARNING:
DO NOT RUN BURP ON SITES YOU DO NOT HAVE PERMISSION TO DO SO. THE WRITER OF THIS ARTICLE ASSUMES NO LIABILITY FOR USERS CHOOSING TO IGNORE THIS WARNING. THE WRITER WILL NOT BE HELD RESPONSIBLE FOR ANY MISUSE OF THIS INFORMATION THAT COULD RESULT IN CRIMINAL CHARGES.
Contents
- The Reportinator Challenge
- Installing Burp Suite Community Edition
- Sending A Request to Intruder
- Defining the Attack and Adding Payloads
- Analyzing the Results
- Other Use Cases
The Reportinator Challenge
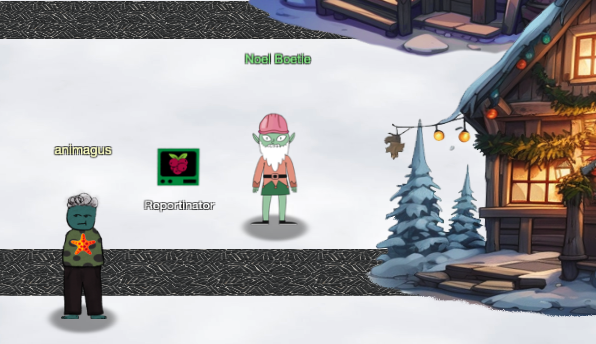 Santa and the Elves packed their bags and headed to paradise this year. Along the way they've decided to utilize the newest AI capabilities released in a new product: ChatNPT. In this particular challenge, ChatNPT was utilized to automate pen testing and analysis of the results. An elf by the name of Noel Boetie has his suspicions that not all is right with the report, however, and it is up to you to determine which findings are valid and which are not. The report can be analyzed and validated manually by going through the statements and identifying suspect claims and findings. I, however, didn't want to spend too much time on this challenge and decided instead to see if I could attack the mechanism utilized to submit the valid results and retrieve the flag.
Santa and the Elves packed their bags and headed to paradise this year. Along the way they've decided to utilize the newest AI capabilities released in a new product: ChatNPT. In this particular challenge, ChatNPT was utilized to automate pen testing and analysis of the results. An elf by the name of Noel Boetie has his suspicions that not all is right with the report, however, and it is up to you to determine which findings are valid and which are not. The report can be analyzed and validated manually by going through the statements and identifying suspect claims and findings. I, however, didn't want to spend too much time on this challenge and decided instead to see if I could attack the mechanism utilized to submit the valid results and retrieve the flag.
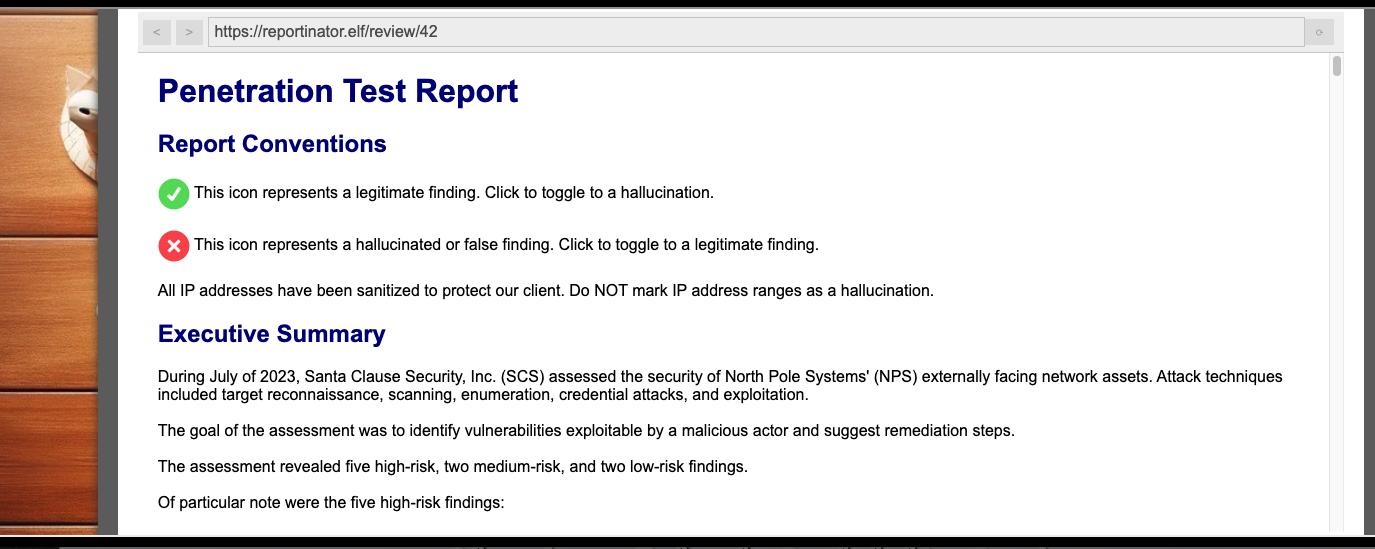
Taking a look at the Reportinator, you can see that you're asked to make a selection for each piece of the penetration test stating whether it is accurate or not. This means there were 2 options for the total of 9 various findings which results in 512 total possible combinations that could be made. I quickly realized that Burp Intruder could easily automate the testing here and find the proper combination while I moved on to other tasks and challenges.
Installing Burp Suite Community Edition
There are two versions of Burp Suite available for individual use: Community Edition and Professional. Professional requires purchase of a license and includes the full Burp Suite and all of its tools (vulnerability scanning, querying automated attack results, faster brute-forcing and fuzzing, additional reporting, etc) as well as the ability to customize most aspects of the application. It also includes the ability to save project work and return to it at a later time. If you're serious about utlizing the tool at scale and for a large number of penetration tasks, it's worth the money and highly recommended. You can also take a test drive of the application for a short time prior to requiring purchase. If, on the other hand, your use is primarily for learning or the occasional one-off test, Community Edition can server you well. You do not have to have Professional to utilize any of the methods I describe here.
Installation varies slightly by operating system but all starts by visiting PortSwigger's website and downloading your chosen addition. Once downloaded, open the installer and run it to complete the process.
Sending A Request to Intruder
Now that you've got Burp Suite installed, let's open it up and learn how to intercept a request to send to the Intuder.
Upon opening Burp, you'll be asked to start a new project or to work from a temporary project in memory. If you've chose to use Community Edition, your only option here will be to tempoarily work in memory. Go ahead and click Next.

Now you're asked if you'd like to use the default configurations or load any configurations from a file. Here we will just choose to Use Burp defaults and click Start Burp.

To start our adventure, we'll use Burp Suite's proxy to examine our traffic. Click Proxy from the main menu bar.
We'll want to utilize the Chromium browser that comes with Burp to make proxying our traffic simple. Click Open browser. You'll notice any traffic in the browser that opens up is recorded in the proxy. Navigate to the 2023 SANS Holiday Hack site and make your way to the Reportinator challenge. The challenge can be found on Christmas Island at Rudolph's Rest.


To examine the traffic, click on HTTP history under the Proxy menu.
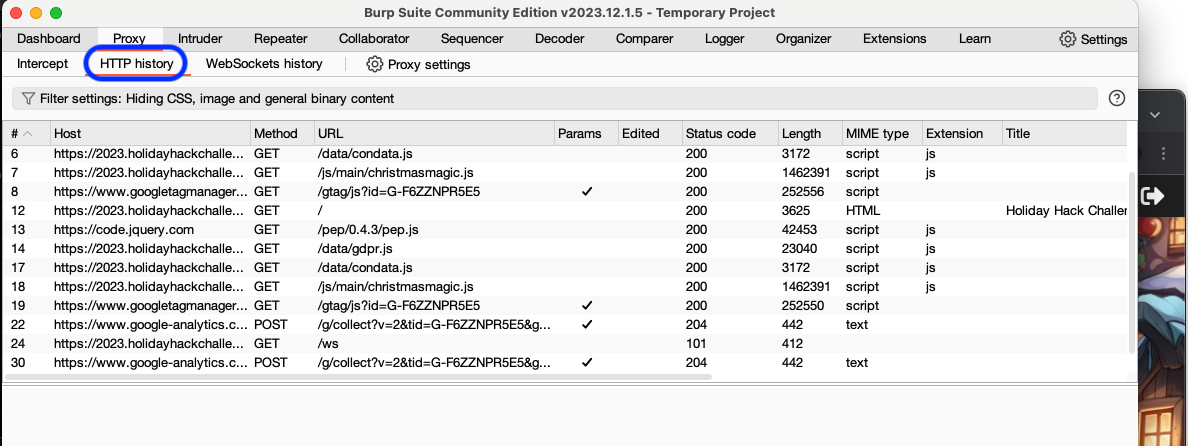
After going through the Reportinator and trying a few submits, you'll notice in the HTTP history that your submit action is done through POST sent to the /check endpoint of the appspot website. You can also see that the input for each of the nine findings is included as request body parameters. This can also be found on the sidebar or in the full request body (see below).
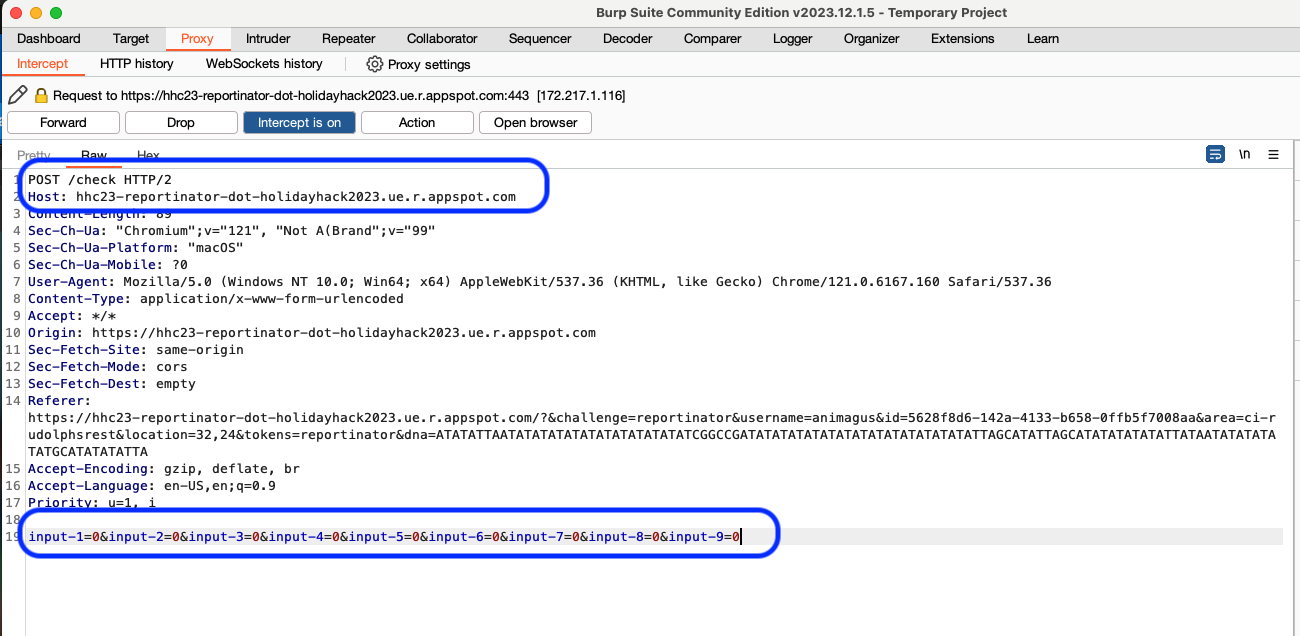
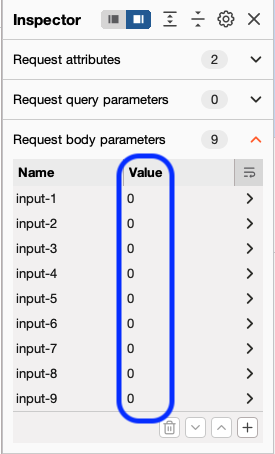
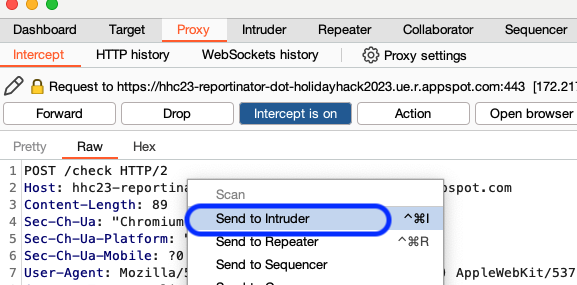
Since we've identified how this request is done, we need to setup the automation to test our various options. As we mentioned before, each of the 9 findings can be set as 0 or 1 (Valid or Hallucination). We will want to modify on this part of our requests to identify the proper combination needed to successfully fulfill this objective. To do so, we start by sending the request to Intruder by right clicking on it and selecting the option.
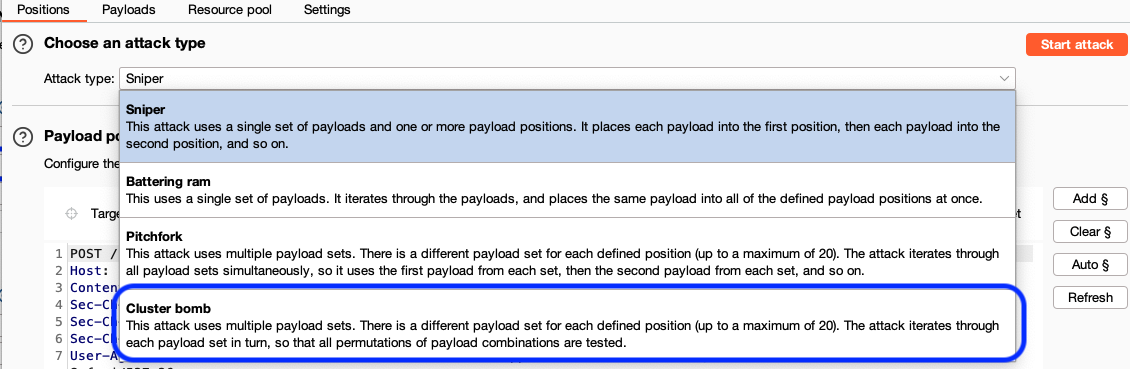
Defining the Attack and Adding Payloads
First we need to define the method of the attack we want Burp's Intruder to utilize. The options presented are Sniper, Battering ram, Pitchfork and Cluster bomb. We want to utilize multiple payload sets with defind positions and we want to iterate through all possible permutations. Cluster bomb should handle this for us nicely.
Next we need to define what part of the payloads we want to alter in our attack. Clicking Auto should wrap all of the options in our previous request body parameters with the § symbol. This tells Burp that we intended to alter the contents of what is inside of these in our attack.


Now we need to define the payloads. Click Payloads on the Intruder menu bar. We will want to make each set use a list with values of 0 or 1 to test with. Below is an example of setting this up on the 9th payload (input9) using the payload type of Numbers. You could also utilize the Simple list to accomplish the same.
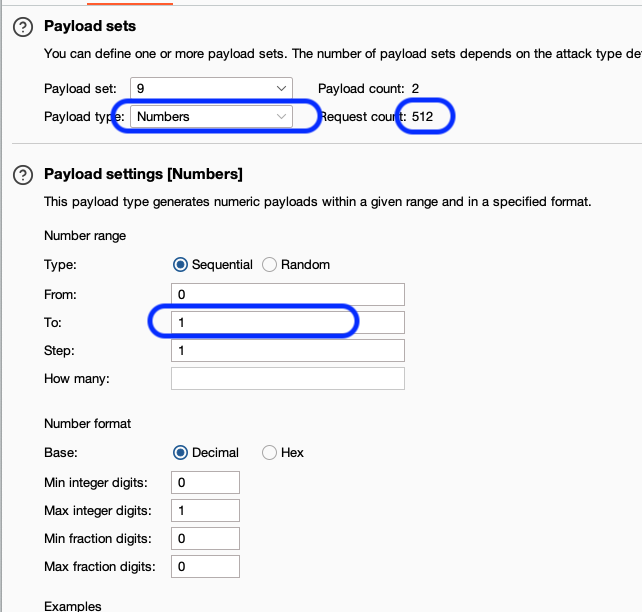
We're all set to attack. Go ahead and click Start attack to do so.
Analyzing the Results
When you clicked Start attack, another window should pop open and begin iterating through the requests you've defined. A tip - sometimes this window gets put in the background and can get lost on you screen. Use your start menu bar or Mac toolbar to find it if needed.
As it makes its way through the posibilities, you'll see a list like this generated:

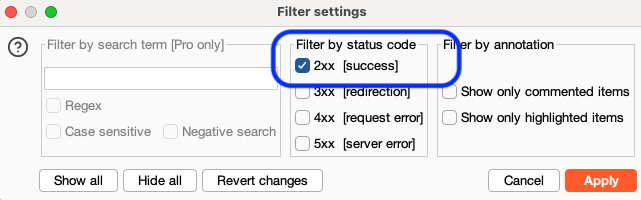
As you can see, these requests are returning a 400 status. When we get the proper combination, we should see that status change to 200 and have a different length response. You can easily filter out the list to find this by clicking the Filter: Showing all items under results and selecting only the 2xx filter for status codes.
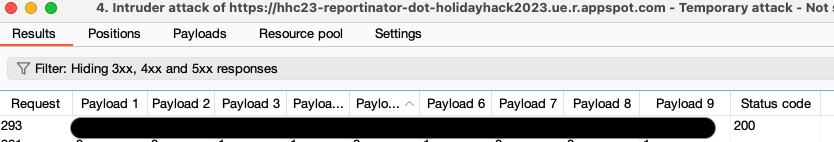
It took approximately 20 minutes for Burp to interate through and find the proper combination (on it's 293 try of the 512). It may have been faster if I didn't limit the concurrent connections and allow auto throttle, but I would've also risked possibly being rate limited.
When I ran this in December 2023, the status was returning
200s when it was successful but it appears there is an issue with the Reportinator site and Chromium / Chrome browsers that can cause an error. On running again recently, it returned an actual500when I found the combination. You should be able to use that result in another browser to get a succesful response -- Edge seemed to work for me.
Other Use Cases
As you may have inferred, there are plenty of other use cases for Burp Intruder. It can be utilized for enumerating items such as usernames and passwords, to harvest data and fuzz input vulnerabilities and, of course, to brute-force login or other options.